How to Install the YARA Malware Analysis Tool On Windows
YARA, which stands for “Yet Another Recursive Acronym” or “Yet Another Ridiculous Acronym“ a play on the fact that the information technology space is full of acronyms. It is an indispensable tool designed to identify and classify malware and other suspicious elements based on defined patterns and rules. YARA is a powerful and versatile open-source tool maintained by VirusTotal, empowers users to bolster their cybersecurity posture through the creation of YARA rules. YARA rules are text-based patterns that describe characteristics of files, such as specific byte sequences, strings, regular expressions, and more. These rules are used to identify and classify files based on the presence of these patterns. By enabling users to create custom YARA rules that match specific characteristics of malicious files, YARA empowers you to proactively detect and mitigate potential threats, minimizing the risk of security breaches and data loss.
In this comprehensive guide, we will delve into the step-by-step process of installing YARA on the Windows operating system. From setting up the necessary prerequisites to executing the installation seamlessly, you'll gain valuable insights into harnessing the power of YARA for your security endeavors. Whether you're a seasoned professional or new to the realm of cybersecurity, these user-friendly instructions will equip you with the knowledge you need to successfully integrate YARA into your Windows environment.
By the end of this tutorial, you'll have a clear understanding of how to harness YARA's capabilities to create custom rules, scan files and directories, and fortify your system's defenses against potential cyber threats. So, let's embark on this journey to enhance your Windows security through the effective installation and utilization of YARA. Your digital safety is our priority, and YARA is the tool that will help you achieve that peace of mind.
Exploring the Windows YARA Package
Since this is a guide on how to install YARA on Windows we’ll use the Windows Package Manager (WinGet) to interact with the VirusTotal.YARA package. If you’re not familiar with this package manager I’ve written a tutorial on how install and use WinGet. Before installing the VirusTotal.YARA package let’s search and show information on this package from the Windows package registry.
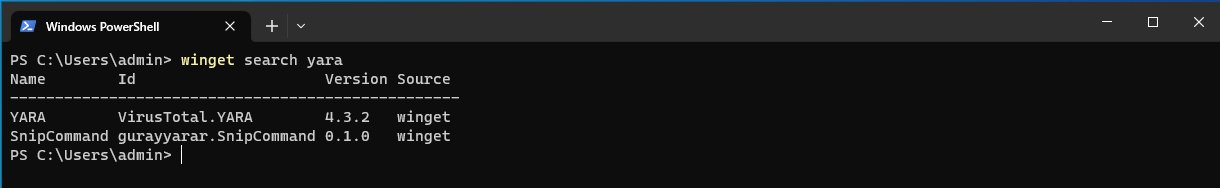
winget search yara
Let’s use the winget search command to see which packages in the Windows package repository contain the keyword YARA. We can perform a simple search using the following command.
winget search yara
The output of this command will show use which files match our keyword of yara as well as return information such as the name, id, version, and source of the Windows package.
Output of the winget search yara command
Based on the above output we can determine that VirusTotal.YARA is the package we are interested in installing. Before we install this package however let’s explore this package before we simply run the install command.
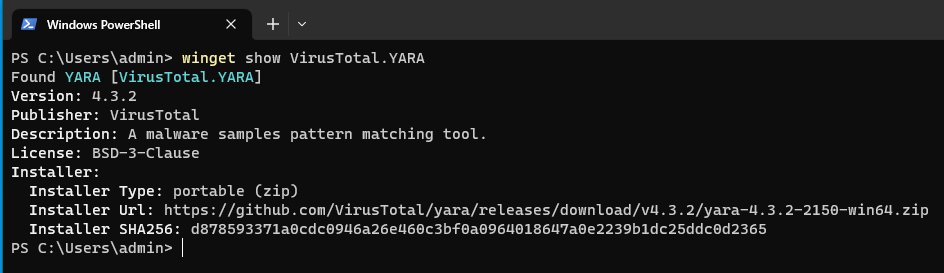
winget show VirusTotal.YARA
We can explore the Windows package manifest file of our package by running the winget show command.
This command provides users with comprehensive display of metadata, including the package name, version, publisher, description, installation and uninstallation commands, and more. Winget show provides a great way to get a general overview of the application.
Installing VirusTotal.YARA
Once we’ve confirmed some of the details regarding this application such as Installer URL, potential security issues, and the SHA256 hash of the package we can download and install this package using WinGet.
winget install VirusTotal.YARA
The winget install command is designed to simplify and expedite the process of installing software applications on Windows systems.
To install the YARA Windows application we’ll first elevate our terminal with gsudo.
gsudo
Once our shell is elevated we can proceed to install the YARA Windows package using the below command.
winget install VirusTotal.YARA
Using this command streamlines the YARA installation process and automatically retrieves the latest version of the requested software from the Microsoft Store, other registered repositories, and in our case GitHub.
Output of the winget install VirusTotal.YARA command
During the installation process we notice that Windows adds two environment variable aliases, modifies our Windows Path, and asks us to restart our shell. Congrats you’ve successfully installed YARA on Windows!
Exploring YARA Tools on Windows
Once installation is complete let’s explore some basic usage as well as how to find help. To start you may have noticed that during the YARA installation process Windows added two new aliases, yara and yarac. Let’s briefly explore what these are.
yara vs. yarac
yara is the main command-line utility that allows users to create and apply YARA rules. The yara command is used to scan files or directories against a set of YARA rules and produce matching results.
yarac on the other hand, is the YARA compiler. It is used to compile YARA rules into a binary format that is optimized for faster pattern matching. The compiled rules produced by yarac can then be loaded and used by the yara command-line utility for scanning files more efficiently. The use of yarac is particularly helpful when dealing with a large number of rules or when performance is a priority especially with rules handling regular expressions.
Using the yara Command-Line Utility
The yara command-line utility follows as simple syntax:
yara <OPTIONS> <RULE> <FILE|DIR|PID>
Let’s demonstrate the yara command-line utility by scanning the wmlaunch.exe binary. This binary is the Windows Media Player launcher and shipped with every Microsoft Windows install. We’ll be using the following rule which is a simple yara rule that detects portable executable (pe) file types.
We can use the following powershell command which uses the Invoke-WebRequest command to download a is_pe.yara from GitHub to our current directory.
Invoke-WebRequest "https://gist.githubusercontent.com/gothburz/ca566694bcf044fcd089cf49f1490edf/raw/dd9cf18c01a735b7bb5af1af6677691fbc3567de/is_pe.yara" -UseBasicParsing -OutFile "is_pe.yara"
Once we have the is_pe.yara file downloaded we can scan the wmlaunch.exe with this rule using the following command.
yara .\is_pe.yara 'C:\Program Files\Windows Media Player\wmlaunch.exe'
Output of the yara command
If a match is found the rule name as well as the matching file will be outputted to the terminal. You have now successfully ran yara on Windows to find malicious files!
Yara Usage, Options, & Help
If you’d like to explore more usage options, syntax, as well as general helpful information regarding the usage of the yara command-line applications using the —help option is a good idea.
Using the yarac Command-Line Utility
As covered previously the yarac utility is the command-line application that compiles yara rules into a binary format for speed and efficiency. The yarac syntax is simple:
yarac <OPTIONS> <SOURCE_FILE> <OUTPUT_FILE>
Let’s use the yarac tool to compile our is_pe.yara file into a binary file.
yarac .\is_pe.yara is_pe.yarac
Once compiled we can test our new compiled .yarac file using the yara application. It’s important to note that in order to pass compiled yara rules to the yara application we must pass the --compiled-rules command-line option.
yara --compiled-rules .\is_pe.yarac 'C:\Program Files\Windows Media Player\wmlaunch.exe'
Output of the yara command against compiled rules
Great! You have now successfully compiled a .yara file into a binary file and scanned an executable file using a compiled ruleset. As covered previously compiling yara files into binary files is a great method of speed, performance, and efficiency is a concern. This is particularly useful with files that contain a large number of yara rules or rules that contain expensive pattern matching methods such as regular expressions.
Yarac Usage, Options, & Help
If you want to explore yarac usage information or need help regarding syntax using the —help flag is a great idea.
yarac --help
Output of the yarac —help command
Conclusion
In conclusion, YARA stands as a crucial asset in the realm of cybersecurity, providing a value tool in the ever-evolving digital threat landscape. Using YARA gives us the ability to identify and classify malware and suspicious elements, YARA serves as a guardian for your digital environment. The power lies in your hands to create custom YARA rules, enabling you to proactively detect and mitigate potential threats, thereby reducing the risk of security breaches and data loss. The versatility and effectiveness of YARA make it an indispensable tool for individuals, blue teams, and organizations alike, empowering them to take a proactive stance against cyber threats.
As we wrap up this comprehensive guide to installing YARA on the Windows operating system, we invite you to take action and implement the insights you've gained. By integrating YARA into your security strategy, you'll be better equipped to safeguard your digital assets and sensitive information. Whether you're a cybersecurity expert or just starting on this journey, the instructions provided will pave the way for a seamless installation process and get you started on using YARA in your own environments. Your commitment to enhancing your Windows security is a vital step towards a safer digital landscape. Embrace the power of YARA and join the ranks of those who prioritize digital safety – together, we can fortify our systems and stay one step ahead of potential threats.
If you need assistance with the installation or usage of YARA, please don't hesitate to get in touch through social media or contact me directly. I’m here to help!